By
Gigabit Systems
January 19, 2026
•
20 min read
Britain’s Digital Spine May Already Be Compromised
Britain may be weeks away from approving one of the most consequential intelligence risks of the decade.
And it’s buried underground.
London isn’t approving a building.
It’s approving permanent proximity to the nervous system of its economy.
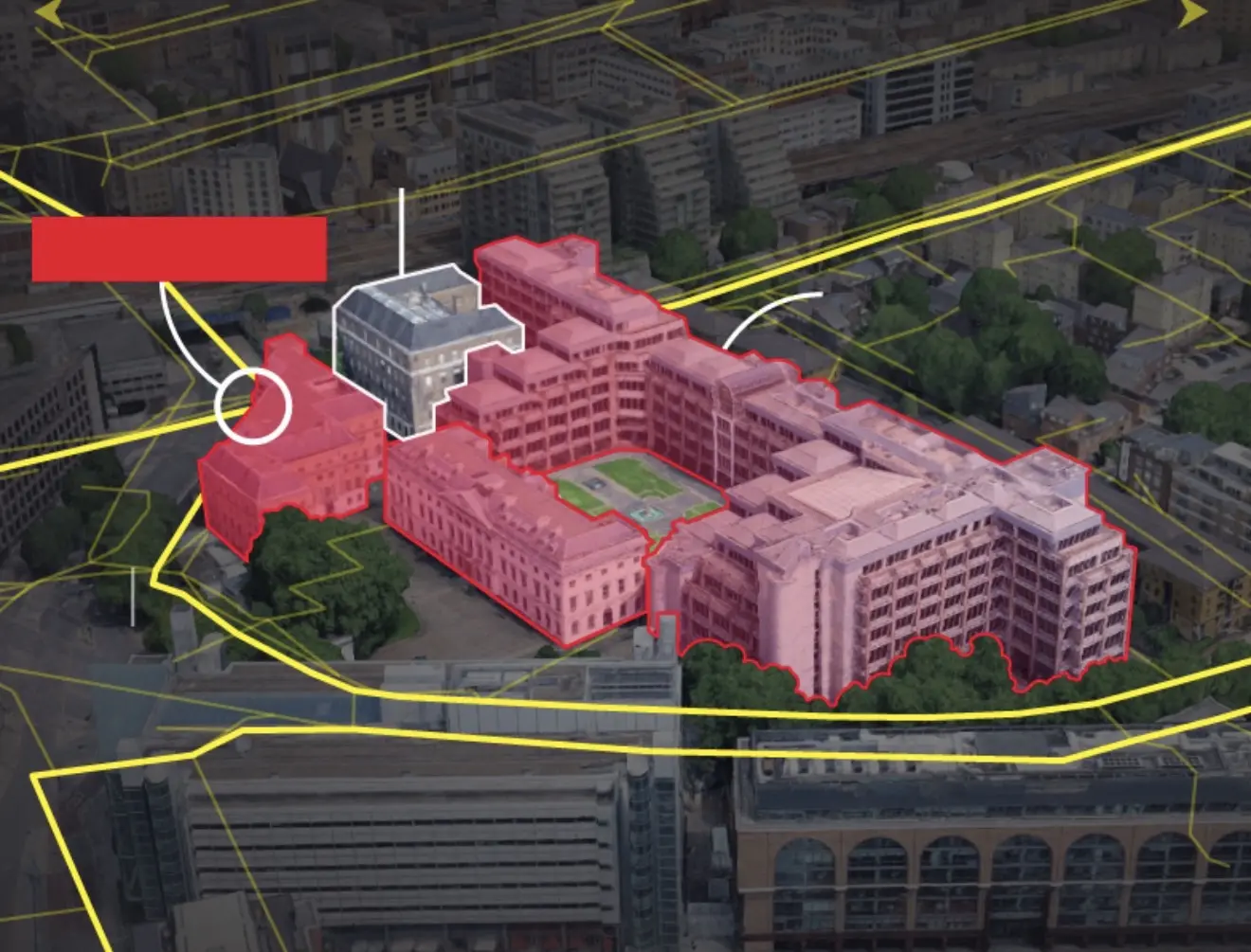
Recently unredacted blueprints for China’s new super embassy reveal a concealed underground complex built within three feet of fiber-optic cables that silently carry Britain’s financial transactions, corporate communications, and internet traffic.
Once concrete is poured, this risk doesn’t fade.
It fossilizes.
This Isn’t Espionage Theater. It’s Infrastructure Physics.
Fiber-optic cables are not abstract technology.
They are physical objects. They emit light. They leak signal.
And when you stand close enough, you don’t need to break encryption.
You just listen.
These cables transport:
Interbank transactions
Trading signals and liquidity flows
Corporate communications
Cloud traffic for millions of users
The UK government has reassured allies that these lines don’t carry classified government data.
That reassurance misses the real threat.
Economic intelligence is national power.
Metadata Is the Weapon Nobody Sees
Modern intelligence agencies don’t need message contents.
They need patterns.
With sustained access to traffic flow, a foreign power can infer:
Market stress before collapses
Capital flight during political instability
Corporate deal timing
Supply-chain pressure points
Financial institution exposure
You can map the future without reading a single word.
The “Secret Room” Changes Everything
The unredacted plans show far more than a basement.
They show intentional permanence.
Beneath the proposed embassy at the former Royal Mint site—the future largest Chinese embassy in Europe—documents reveal:
208 concealed rooms
Hot-air extraction systems, consistent with heat-dense computing
Emergency generators and showers, enabling extended underground occupation
Dedicated communications cabling
This is not diplomatic back-office space.
This is a hardened environment designed to operate quietly, continuously, and independently.
That combination—
physical access + compute + time—
is the holy trinity of modern intelligence operations.
“An Enormous Temptation”
According to Alan Woodward, a professor of cybersecurity at the University of Surrey, the decision to demolish and rebuild a basement wall next to the cables is a glaring red flag.
His assessment was stark:
“If I were in their shoes, having those cables on my doorstep would be an enormous temptation.”
In intelligence work, temptation matters—because capability already exists.
Once Built, The Risk Becomes Permanent
This is the part most people miss.
You cannot “inspect harder” once fiber is buried beneath concrete.
You cannot rotate cables away from a completed structure.
You cannot audit light leakage underground.
Once access is granted, the exposure is structural.
This isn’t a breach you patch.
It’s an attack surface you authorize.
The Timing Raises Alarms Across Allied Intelligence
The unredacted plans surfaced just days before Keir Starmer is expected to approve the project ahead of a diplomatic visit with Xi Jinping.
At the same time, Britain has reportedly been pressured to reassure intelligence partners—including the United States—that no sensitive data is at risk.
But intelligence alliances are built on trust, not assurances.
And trust erodes quickly when physical-layer risks are dismissed as theoretical.
This Is How Modern Power Operates
Espionage today doesn’t wear trench coats.
It looks like:
Strategic real estate placement
Long-term physical access
Legal diplomatic cover
Plausible deniability
As shadow national security minister Alicia Kearns warned, approving the embassy would hand Beijing a “launchpad for economic warfare.”
That isn’t hyperbole.
That’s doctrine.
Why This Matters Beyond Britain
This isn’t just a London story.
It’s a global warning for:
Governments approving foreign construction near infrastructure
Cities trading short-term diplomacy for long-term exposure
Organizations that think cybersecurity begins with software
It doesn’t.
Cybersecurity begins where cables run
—and who stands next to them for decades.
Once infrastructure is compromised, everything built on top inherits the risk.
The Quietest Breaches Are the Most Dangerous
There may never be a smoking gun.
No leaked memo. No intercepted call.
Just markets that move before news breaks.
Deals that fail before negotiations surface.
Pressure applied before anyone understands why.
That’s what makes this frightening.
If this risk is approved, Britain won’t hear the breach.
It will feel it later.
70% of all cyber attacks target small businesses, I can help protect yours.
==============================
Follow me for mind-blowing information and cybersecurity news. Stay safe and secure!
#CyberSecurity #NationalSecurity #InfrastructureProtection #Espionage #Geopolitics