By
Gigabit Systems
December 23, 2025
•
20 min read
Your WhatsApp Can Be Hijacked Without Hacking Anything
A New Account Takeover That Bypasses Passwords Entirely
Security researchers are warning WhatsApp users about a growing attack technique that doesn’t break encryption, steal passwords, or bypass authentication.
Instead, attackers abuse a legitimate WhatsApp feature — device linking — to quietly attach their own browser to a victim’s account.
Once linked, the attacker gains full real-time access:
Read messages as they arrive
Download shared media
Send messages as the victim
Spread the attack to contacts and group chats
No password cracking required.
How the “GhostPairing” Attack Works
This attack chain relies entirely on social engineering, not technical exploits.
Step 1: A Trusted Message
Victims receive a short message that appears to come from a known contact.
It often says something simple like:
“Is this you in this photo?”
The link preview frequently mimics Facebook content to build trust.
Step 2: A Fake Login Page
Clicking the link redirects the user to a fake Facebook login page hosted on a lookalike domain.
But instead of authenticating anything, the page silently initiates WhatsApp’s device-pairing workflow.
Step 3: Legitimate Pairing, Malicious Intent
The victim is prompted to enter their phone number.
WhatsApp then generates a real pairing code.
The attacker displays that code on the fake site and instructs the victim to enter it inside WhatsApp — unknowingly authorizing a new linked device.
WhatsApp does warn that a device is being added, but researchers report many users miss or misunderstand the message.
Why This Attack Is So Dangerous
Once paired, the attacker doesn’t need to stay hidden.
They can:
Monitor conversations indefinitely
Collect sensitive data
Impersonate the victim
Abuse trust in group chats
Launch secondary scams
Because everything looks legitimate, victims often remain unaware for long periods.
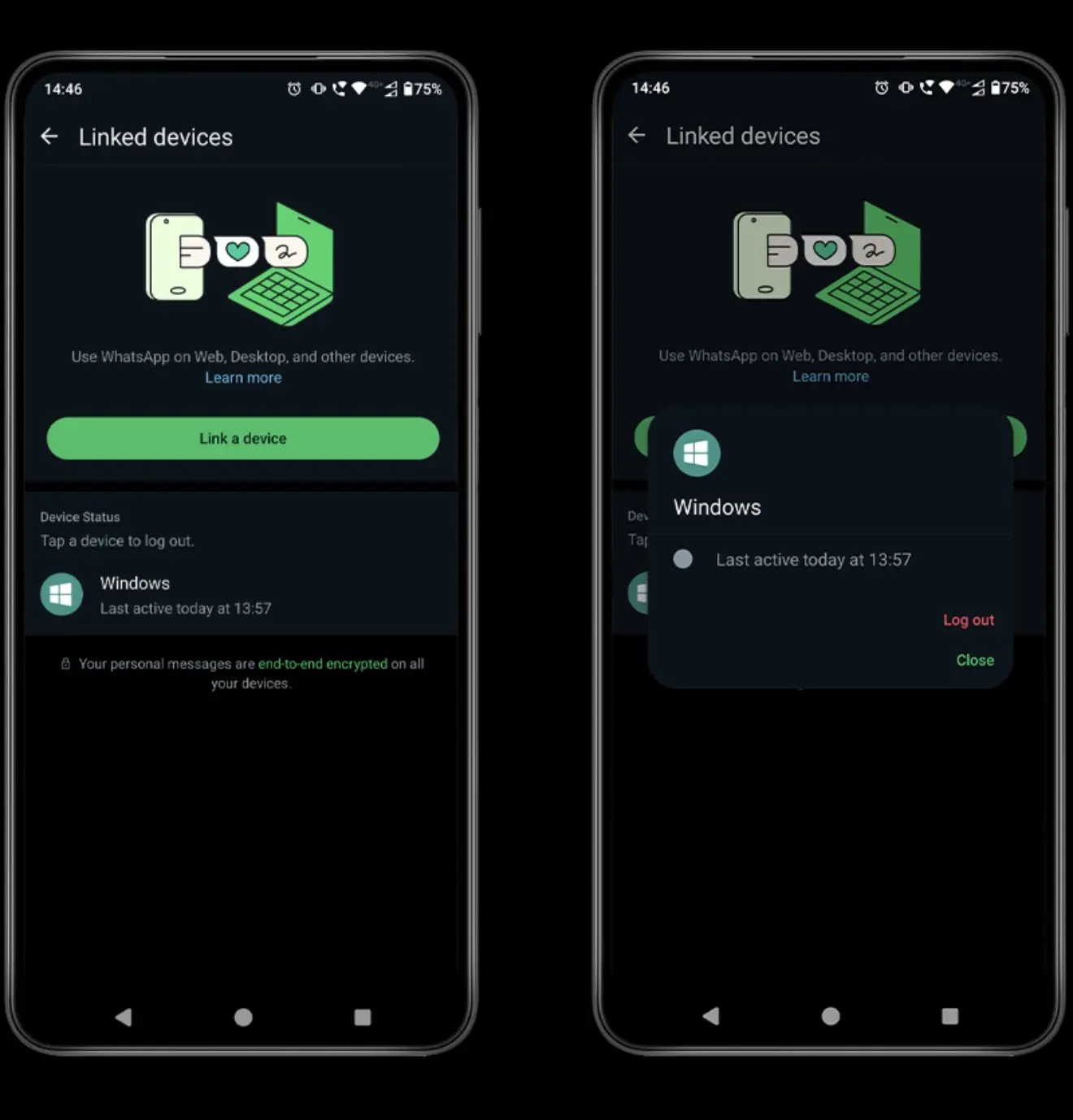
The Only Reliable Way to Detect Compromise
Security researchers agree on one thing:
The Linked Devices section is the only reliable indicator of compromise.
To check:
Open WhatsApp
Go to Settings → Linked Devices
Review every listed device
If you see anything you don’t recognize, remove it immediately.
How to Protect Yourself
WhatsApp users should take the following steps now:
Regularly review Linked Devices
Enable WhatsApp two-step verification
Never enter pairing codes from websites
Be suspicious of “photo” or “video” lures
Report suspicious messages
Avoid logging into Facebook or WhatsApp via unknown links
Antivirus tools can help block malicious sites, but they cannot prevent social-engineering authorization once the user approves it.
Why This Matters for SMBs, Healthcare, Law Firms, and Schools
WhatsApp is widely used for:
Internal coordination
Client communication
Group discussions
Informal operational updates
A single compromised account can expose:
Sensitive conversations
Client data
Internal planning
Contact networks
Encryption does not protect against authorized abuse.
The Provocative Takeaway
You don’t need your password stolen to lose your account.
You just need to approve the wrong device once.
In modern attacks, trust is the exploit.
70% of all cyber attacks target small businesses, I can help protect yours.
#️⃣ #cybersecurity #WhatsApp #accounttakeover #MSP #socialengineering